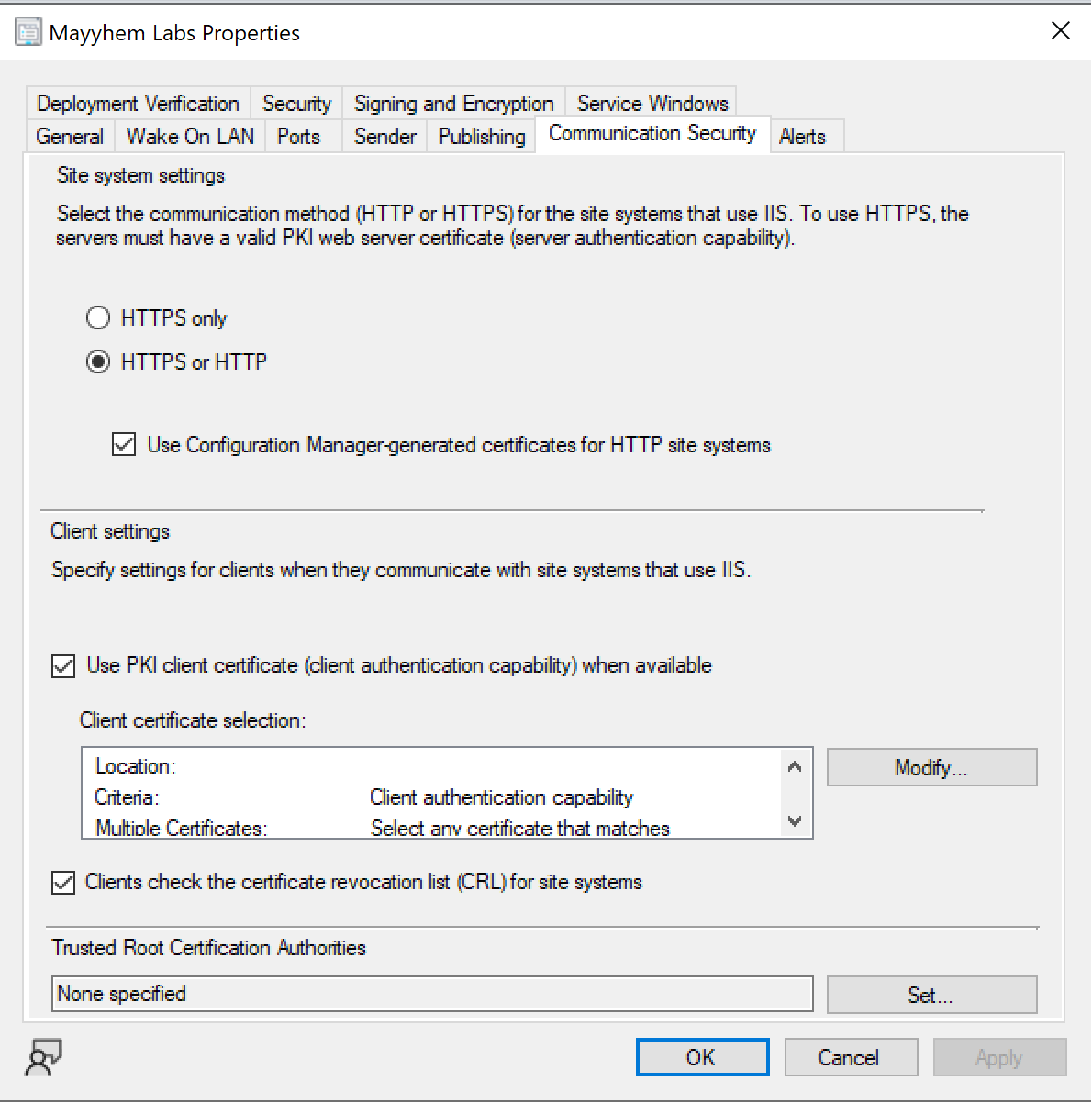
Summary
When PKI certificates are required for client authentication, the client must use a valid, trusted certificate to authenticate communications with management points. As a result, self-signed certificates created by an attacker can’t be used to register rogue devices in SCCM to request policies or abuse automatic client push installation. This can allow recovery of plaintext domain credentials or coercion of NTLM authentication from configured installation accounts and the site server’s domain computer account, which can be relayed to compromise other systems where the accounts have administrator privileges. To begin planning the transition to requiring PKI certificates for client communications, follow Plan for PKI certificates in Configuration Manager. You can view current settings atAdministration > Overview > Site Configuration > Sites > Properties > Communication Security. Configure HTTPS only only after confirming that all clients in the environment are able to communicate with management points using PKI certificate.
Linked Defensive IDs
Associated Offensive IDs
- CRED-2: Request machine policy and deobfuscate secrets
- ELEVATE-2: NTLM relay via automatic client push installation
References
- Chris Thompson, Coercing NTLM Authentication from SCCM
- Microsoft, Plan for PKI certificates in Configuration Manager